Securing Your Cloud: Best Practices for Data Protection in a Cloud Environment
As businesses increasingly embrace cloud computing to drive innovation and agility, safeguarding data in the cloud has become a top priority.
While the cloud offers numerous benefits, including scalability, flexibility, and cost-efficiency, it also introduces unique security challenges that organizations must address to protect sensitive information and maintain compliance.
Personal Data covered under privacy regulations
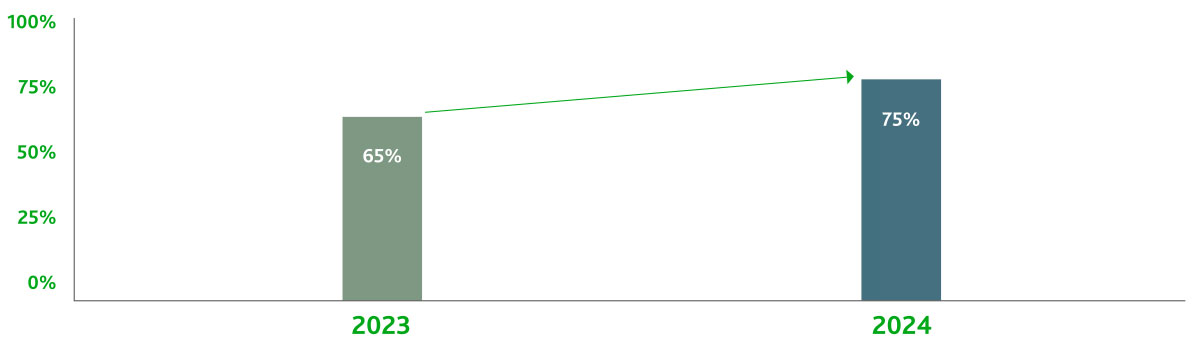
By 2024, Gartner predicts that an even greater portion of the world, exceeding 75% as opposed to 65% in 2023 will have its personal data covered under privacy regulations
At Kalaam Telecom, we understand the importance of cloud security, and in this blog post, we’ll explore best practices to safeguard your data in a cloud environment.
Understanding Cloud Security Challenges
Data Breaches
Unauthorized access to data remains a significant concern in the cloud, whether through malicious attacks, insider threats, or misconfigured access controls. Data breaches can result in financial losses, reputational damage, and regulatory penalties, underscoring the importance of robust security measures.
Compliance Risks
Many industries are subject to stringent regulatory requirements regarding data privacy and security, such as GDPR, HIPAA, and PCI DSS. Additionally, adhering to frameworks like the Cloud Control Matrix (CCM) recommended by the Cloud Security Alliance (CSA) can further strengthen your cloud security posture.
Shared Responsibility Model
Cloud providers operate under a shared responsibility model, where they are responsible for securing the underlying infrastructure, while customers are responsible for securing their data and applications. Understanding this shared responsibility is essential for implementing effective security measures and mitigating risks effectively.
Cloud Security Trends
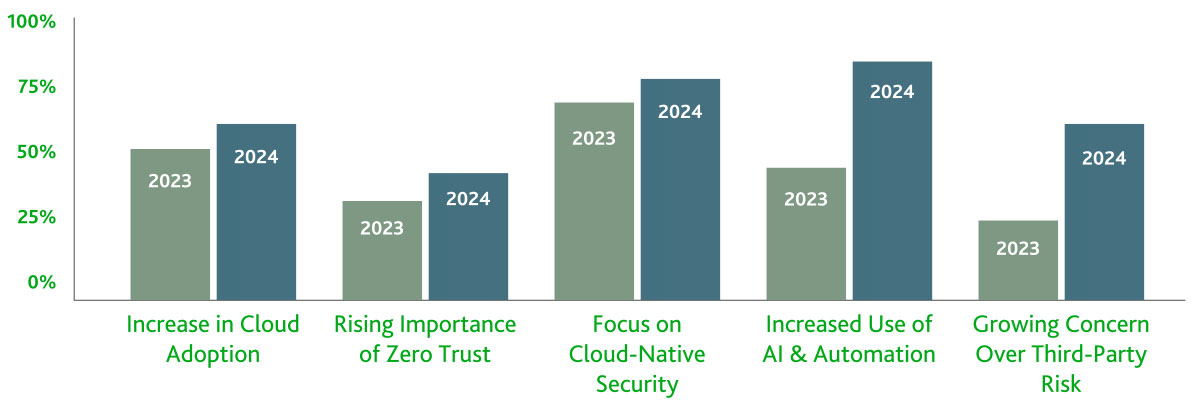
Best Practices for Cloud Security
- Encrypt Data: Encrypting data at rest and in transit is fundamental to protecting sensitive information from unauthorized access. Implement strong encryption algorithms and key management practices to ensure data confidentiality and integrity, reducing the risk of data breaches and unauthorized disclosures.
- Implement Access Controls: Enforce least privilege access controls to limit user permissions and restrict access to sensitive data based on job roles and responsibilities. Implement multi-factor authentication (MFA) and identity and access management (IAM) solutions to strengthen authentication mechanisms and prevent unauthorized access.
- Regularly Monitor and Audit: Implement robust monitoring and logging capabilities to detect suspicious activities, unauthorized access attempts, and potential security incidents in real-time. Conduct regular audits and security assessments to identify vulnerabilities, compliance gaps, and areas for improvement, ensuring continuous security posture improvement.
- Backup and Disaster Recovery: Implement regular data backups and disaster recovery plans to ensure data availability and business continuity in the event of data loss, corruption, or ransomware attacks. Store backups in geographically diverse locations and test recovery procedures regularly to verify data integrity and readiness.
- Patch and Update Regularly, with Strong Credentials: Implement a comprehensive approach to keeping your cloud environment secure. This includes regularly applying the latest security patches and software updates to address known vulnerabilities and mitigate security risks, utilizing automated patch management solutions and vulnerability scanning tools to streamline the patching process and enforcing strong credential policies, such as requiring complex passwords and restricting user access based on job functions.
- Data Governance and User Privacy: Establish a robust data governance framework to ensure the proper handling, protection, and access to user data. This includes obtaining informed consent from users for data collection and usage, providing users with access and control over their data and regularly reviewing and updating data governance policies to comply with evolving regulations.
Partnering for Secure Cloud Solutions
The global landscape of data privacy regulations is constantly evolving. By adhering to best practices for data protection, organizations can ensure they are prepared to adapt to these ongoing changes. By adopting best practices for cloud security and partnering with a trusted cloud provider like Kalaam Telecom, organizations can strengthen their security posture, protect sensitive data, and mitigate risks effectively. Together, let’s harness the power of the cloud while ensuring the highest standards of data protection and compliance.
Article by
Pramod Deshpande
Group Sr. Manager – Cloud Services

